Summary of FBI Seminar on Internet Security
FIRST OF ALL
HAPPY THANKSGIVING TO YOU AND YOUR FAMILY!!!!

THEN ….. for all of you who could not attend our recent FBI Cyber Security Seminar, we have prepared a recap of the presentation highlights.
Below is a summary of some of the key points covered by Kimo Hildreth of the FBI Task Force and by George Baldonado, President of Oasis Technology.
If you would like more details on the Vulnerability Scan special we are offering, please call Oasis Technology at 805-445-4833.

Summary of
FBI Seminar on Internet Security
November 14, 2017
Business Email Compromise Workshop: BEC 2017.11.17
Speaker: Kimo Hildreth, Ventura County District Attorney Investigator, FBI Outreach Program
Cyber Security Threat-scape
When you receive email, trust your instincts: If it doesn’t smell right, it probably is fraudulent. Don’t open it. Report it to your IT department.
Between October 2013 and October 2016, Internet losses amounted to 5 billion dollars. Business Email Compromise (BEC) has an average loss of $130,000. The average loss from ransomware is $722. And the average bank robbery generates $3,816 of losses.
Ransomware is getting all of the press, but Business Email Compromise (BEC) is getting away with the lion’s share of stolen funds.
In 2016 businesses and individuals in California lost $255 million — made up of 39,000 victims. $14.6 million per month of Internet fraud in Los Angeles alone.
SMBs (Small Midsized Businesses) make up 54% of US sales. Cyber Criminals attack SMB because it is low risk.
60%of small businesses hit by a threat go out of business within 6 months.
The reason many companies are not protected is because they put profits ahead of security. Naturally, businesses focus their efforts profits. However, this culture needs to change so at least there is a balance between the two.
Beware the Internet of things (IOT). The Internet is NOT secure. Web cams can be opened by a hacker and you will not know. If necessary, cover up your web cam and unplug your microphones.
Real Estate market is prime target. Real estate firms and escrow companies’ emails have been compromised by hackers using a common 4 step process. As part of this process, last minute instructions via valid appearing email redirects company officials to send funds to bogus accounts that funnels money out of the company and out of the country.
Cracking your password gives hackers full access to your entire system.
Using BEC, such as false invoices, false wire transfer request, etc., hackers impersonate businesses or business officials so that it causes the recipient to erroneously wire money to fake locations.
What YOU can do:
- Use strong passwords – a pass “phrase” is a better password than one word.
- Answer secret questions with non-standard answers.
- Use two factor authentications.
- Use different emails and passwords for critical services.
- Keep your systems updated.
- Backup your data.
- Check your system.
- Report issue to BEC. https://www.ic3.gov/media/2016/160614.aspx
Steps For Businesses to Take to Not be Part of the 1 Trillion Dollars of Worldwide IT Intrusion Losses
Speaker: George Baldonado, President and CEO, Oasis Technology, Inc.
Work with an established IT Managed Service Provider offering Cyber Security services.
Oasis Technology has serviced Fortune 500 clients since 1979.
In 2013 it developed and patented the first Artificial Intelligence powered Cyber Security Protection platform.
Recognize “There are two types of companies in the world: those that know they’ve been hacked, and those that don’t.” ….Misha Glenny
Should we believe that all firewalls protect our IT networks? No, they all have vulnerabilities. How do I protect my company and myself?
- Find out how the hackers can get into your network.
- Actively locate your vulnerabilities.
- Stop their entry points.
Recommendation:
- Obtain an external vulnerability scan from an independent, proven, and knowledgeable cyber security firm.
- Have a vulnerability scan. It is quick, non-invasive (your network will not be penetrated) and it will provide you with the information to see where your network has vulnerabilities – and then you can plug the holes.
Do Not Assume!!!!!!!!!!!
Most people believe that their Cyber Security bullet proof like the picture below.
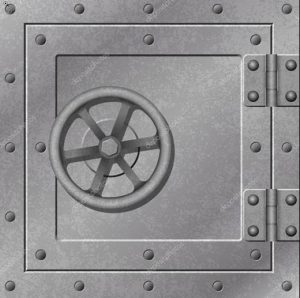
When in TRUE FACT it is really like this:

DO NOT THINK IT CANNOT HAPPEN TO YOU

BECAUSE IT CAN AND IT DOES!!
Remember to stay Cyber Safe!
Get a reputable “White Hat hack” expert to look at your network and perform a “NON-INVASIVE” vulnerability analysis on your network from the outside.
Sounds like I may want to get a vulnerability analysis — what do I do?
- CALL US at 805-445-4833.
- We can even go to your site if you are stuck in rut!!
26 Secrets that an Identify Thief Does not Want You to Know
What an Identity Thief Does Not Want You to Know — Click here
Email: georgeb@oasistechnology.com
Page: www.oasistechnology.com
www.facebook.com/oasistechnology
Voice: (805) 445-4833
Fax (805) 445-4839
601 Daily Drive, Suite 226 ● Camarillo, CA 93010 ● (805) 445-4833
TITAN – The Black Hole that hackers hate and firewalls love www.ipstitan.com/titanshow
There are two types of companies in the world: those that know they’ve been hacked, and those that don’t. …Misha Glenny